Introduction to Security Configuration
Crystal Eye’s security configuration is designed to allow administrators to arrange and fine-tune various security related settings that come as default. The sole objective of these configurations and controls is to facilitate a defence-in-depth strategy.
Gartner Peer Reviews
 Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Creating Traffic Rules, Zones, DNAT Rules & SNAT Rules¶
The Advanced Firewall application can be used to create object-based firewall rules to manage the traffic flow between various zones in the Crystal Eye XDR network.
The advanced features of this application allow CE XDR administrators to create:
-
Default and custom security zones
-
Traffic rules and assign them to security zones
-
Application rules to assign DNAT rules
-
Gateway traffic rules to assign SNAT rules.
The advanced firewall application has numerous default traffic and application rules. In addition to this, the CE XDR also provides options to create customised traffic rules (with actions such as Allow, Reject, Block, IDPS, and Web Filtering) and customised application rules to optimize DNAT rules.
Know more about the Advanced Firewall application here
Anti Bruteforce Attack Forcefield to Protect the Crystal Eye XDR¶
The Forcefield application scans the system for authentication failures across various types of services installed in the system. If the failure threshold is exceeded, the app blocks the attacking system IP address.
Gartner Peer Reviews
 Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Intrusion Protection & Detection¶
The Intrusion Detection and Protection application is built into the in-depth holistic security framework of the Crystal Eye XDR extending its capabilities to protect the network against threats. The IDPS component of the CE XDR actively monitors network traffic and detects anomalies based on the backend and local IDPS rules.
Know more about Intrusion Protection & Detection
Monitoring traffic of Grouped Devices and stopping them from Getting Compromised¶
The Passive Encryption Control application is designed to passively model benign traffic originating from an IoT device. This is defined as the baseline state of a network created during network segmentation. Any behaviour outside baseline activity is flagged and the user can take appropriate actions which includes block traffic, allow traffic, block the IoT device from accessing the internet and/or pinhole a particular traffic to the IoT device.
Know more about Passive Encryption
Gartner Peer Reviews
 Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Secure Web Gateway¶
A Secure Web Gateway (SWG) is a security solution that is designed to provide web security for an organisation's users and devices by enforcing security policies for web traffic. It is used as a tool to achieve Zero Trust by providing an additional layer of security to protect against potential threats.
Some ways in which a Secure Web Gateway can be used to achieve Zero Trust include Identity and Access Management, Web filtering and content control, Increased Detection Engineering Capability and assist in Data Loss Protection (DLP) programs and reporting.
A Secure Web Gateway can be used to enforce Identity and Access Management policies, ensuring that only authorised users and devices are granted access to web resources. This helps to prevent unauthorised access to sensitive data and applications. A Secure Web Gateway should be used to filter web traffic and block access to malicious websites and applications based on strong policy configuration linked to company compliance documents outlined use of assets and asset control.
It can also be used to control access to specific types of content, such as social media or file-sharing websites, that may pose a security risk. Once policies are in place, increased Threat Prevention and Detection can be achieved based on policy configuration A Secure Web Gateway can be used to detect and prevent a range of web-based threats, including malware, phishing, and other types of attacks. It can also provide real-time threat intelligence and analysis to help organisations respond quickly to potential threats.
The Crystal Eye Secure Web Gateway can be a valuable tool for achieving Zero Trust by providing an additional layer of security for web traffic. By enforcing strict security policies and preventing unauthorised access to web resources, organisations can significantly reduce the risk of web-based threats and improve their overall security posture.
Know more about Secure Web Gateway
Gartner Peer Reviews
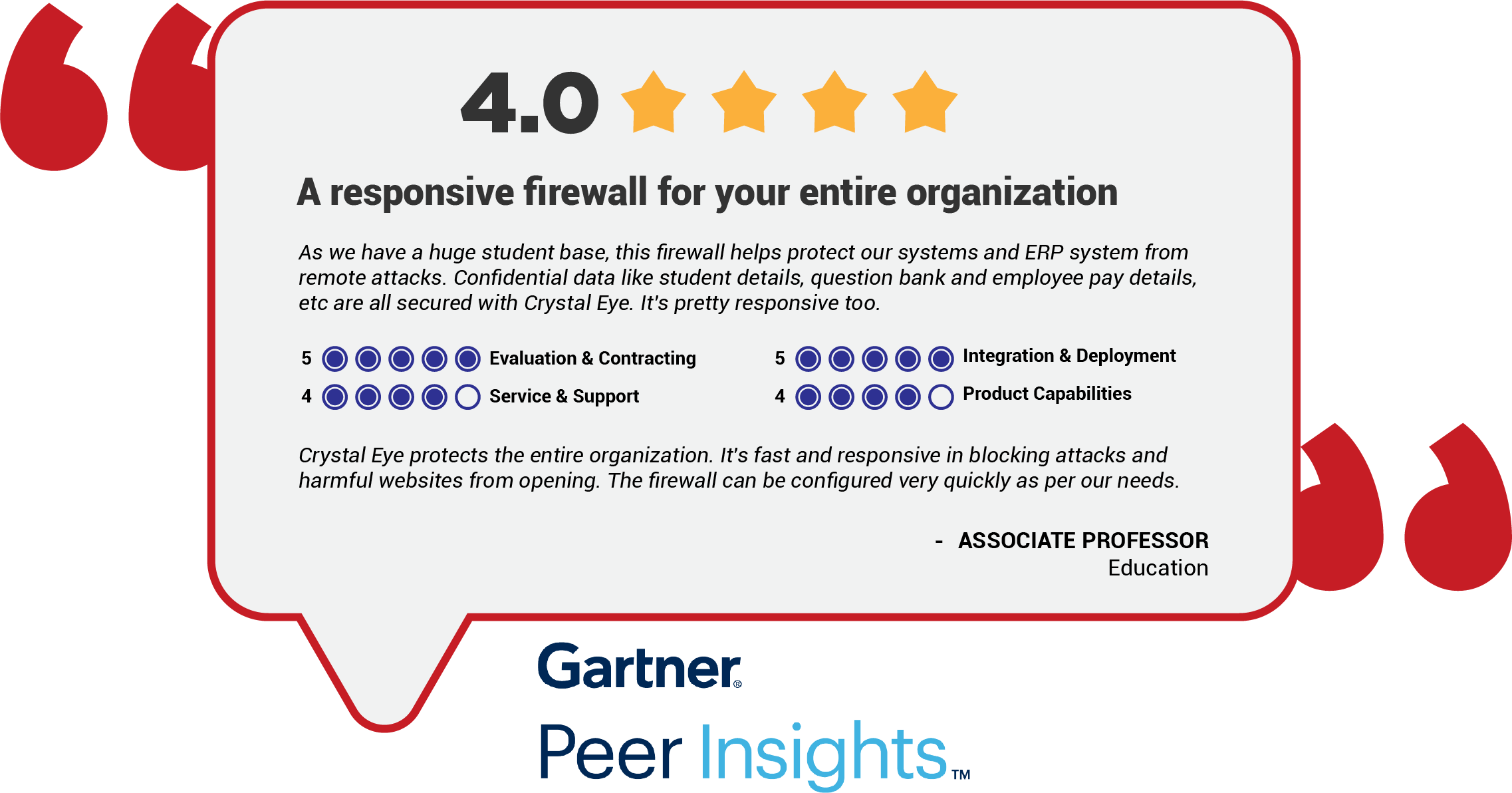 Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Explore more Red Piranha Customer Reviews on Gartner Peer Insights