Introduction to Compliance Controls
The Compliance Controls section are stacked with applications that outlines policies organizations can implement to meet the standards and expectations set forth in the Information Security Management System. A major chuck of this section enables network deployments uplift the continuous approach in improving cyber resilience of organizations through:
- Azure AD integration providing enhanced threat and activity signalling
- Vulnerability Scanning and Integrated Risk Management
- PCAP Analysis
- Data Loss Prevention
Gartner Peer Reviews
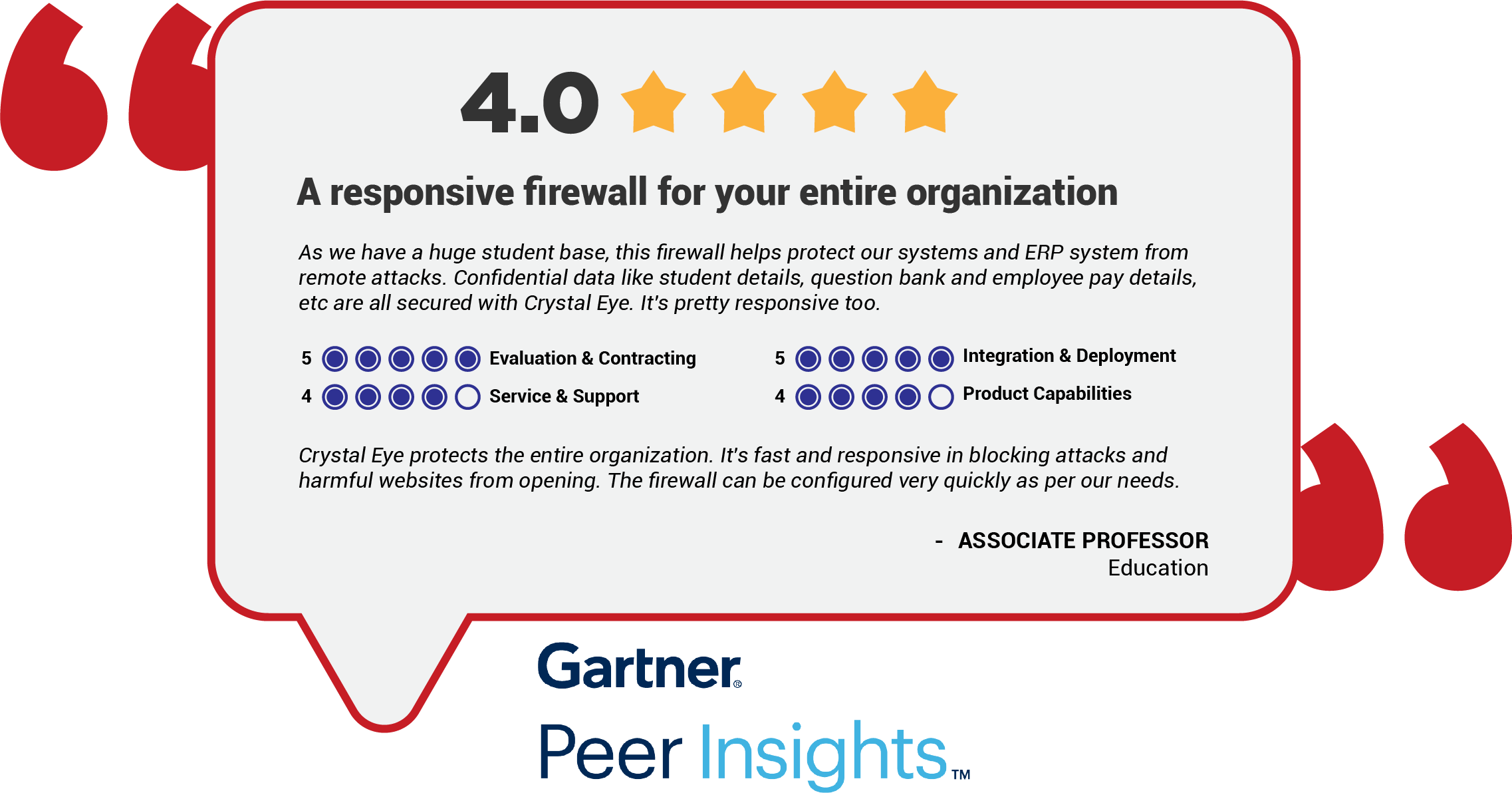 Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Explore more Red Piranha Customer Reviews on Gartner Peer Insights
Azure Active Directory Application¶
Monitoring Azure Active Directory (Azure AD) events can help you track changes and activities in your Azure AD environment. This can be useful for a variety of reasons, such as:
Ensuring the security of your Azure AD environment: By monitoring Azure AD events, you can identify potential security threats, such as unusual login activity or unauthorized changes to user accounts.
Troubleshooting issues: Monitoring Azure AD events can help you diagnose and resolve problems in your Azure AD environment. For example, if you notice a spike in failed login attempts, you can use this information to investigate the cause and take appropriate action.
Auditing and compliance: Many compliance regulations require organisations to track and audit certain activities in their IT systems. Monitoring Azure AD events can help you meet these requirements by providing a record of changes and activities in your Azure AD environment.
Overall, monitoring Azure AD events can provide valuable insights and help you maintain a secure and efficient Azure AD environment.
Data Loss Protection¶
The Data Loss Protection application allows organizations to boost their DLP program designed to provide protection from getting breach.
The DLP app is utilized by DLP program implementers to reduce risks derived from poor business processes. The overall features of the DLP app works as an excellent tool to help organizations comply with ISO 27002:2022 framework, Control 8.12 – Data Leakage Prevention.
An effective DLP program must be built in-line with the controls put in place to classify information based on confidentiality, integrity and availability.
Crystal Eye XDRs DLP application policies can be configured to both Reject and Alert mode providing control over the movement of sensitive data that have been labeled to be protected against exfiltration.
Once the DLP feature is enabled it searches all files located in various computers in the CE network for structured data formats involving credit card numbers and social security numbers (SSN). Thereon, the DLP apps in-built default functionality triggers an alert every time Credit Card Numbers and Social Security Numbers (SSN) are extruded outside CE XDR networks.
PCAP SNAP Application¶
The PCAP Snap app is used to capture network traffic and then transfer it to designated Red Piranha servers for automatic analysis and manual examination. The most convenient aspect of using this application is that it has a phenomenal packet capture scheduler that can be used to add multiple schedules as per requirements.
Running PCAP analysis is done in conjunction with our Security Operations Team during either a breach investigation process or a compliance threat hunting process.
Crystal Eye Attack Surface Reduction (CESAR) Application¶
The Crystal Eye Attack Surface Reduction (CEASR) application ensures devices on your network conform to security policies based on standard security frameworks such as the Australian Signals Directorate's Information Security Manual (ISM) and the Essential Eight guidelines. It also allows CE XDR administrators to apply operating system policies across a range of devices and provide ongoing device monitoring to keep track of your compliance baseline in real-time.
Vulnerability Scanning¶
The Vulnerability Scanning application is a comprehensive vulnerability assessment system that is built to detect, and flag known and potential security weaknesses in servers and user devices located in the Crystal Eye network or elsewhere.
The application has enhanced capabilities to perform vulnerability scan of:
- Servers and user devices in the Crystal Eye network,
- Servers or user devices located outside the Crystal Eye network, or
- Specific website page
The application is programmed to scan all default port types. However, the Crystal Eye administrator can also specify the custom ports to be scanned. The fully automated system of the Vulnerability scanning application enables CE administrators to identify security loopholes in the network and classify weaknesses that might lead to a security incident. It helps in predicting the effectiveness of the various countermeasures taken to secure networks and assists in remediating any risks that are targeted towards external facing servers deployed in the Crystal Eye network.