IP Attack Map
Overview¶
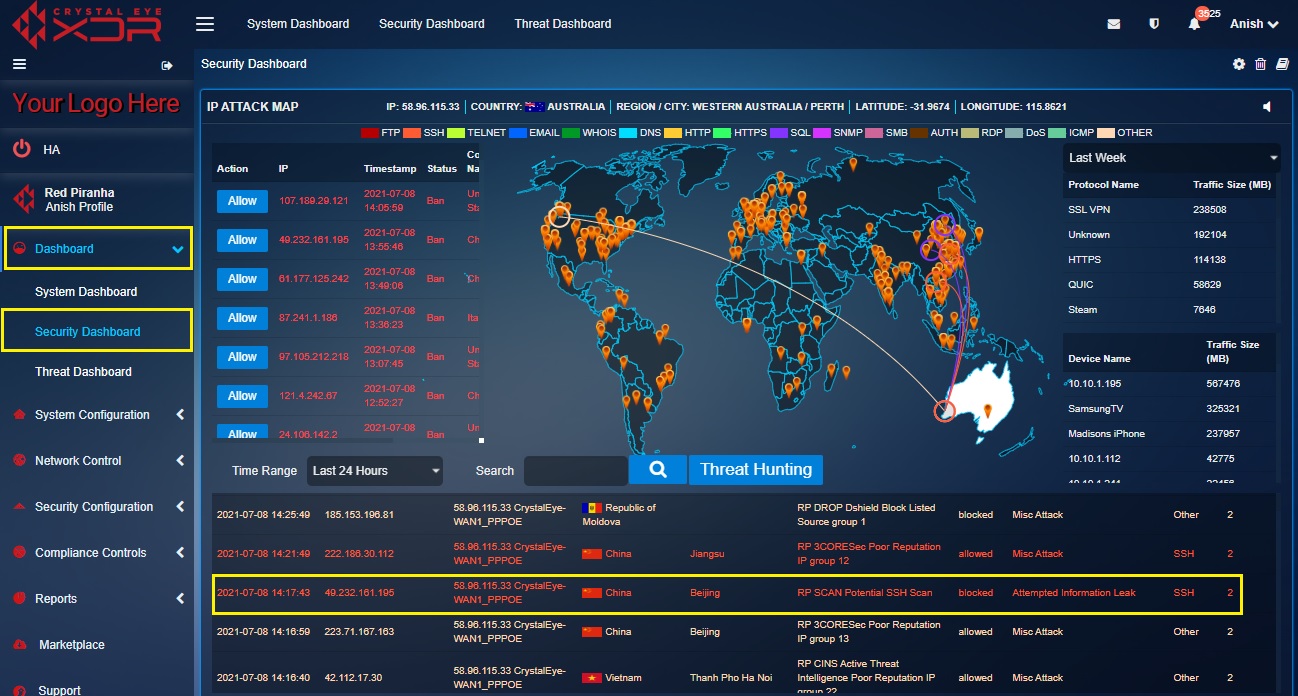
The IP Attack Map section of the Security Dashboard portrays unmatched capabilities in providing a base view of all attacks originating from various IP addresses targeted towards Crystal Eye XDR networks.
There are six major security related indicators that are displayed in the IP attack map section of the CE Security Dashboard:
Banned IPs Table¶
Crystal Eye XDR has an in-built defensive system called ‘Forcefield’ that bans IP addresses in case the authentication failure threshold is surpassed. The Banned IPs table shows the time and date on which the IP address was banned providing deeper insights of possible failed breaches. Crystal Eye XDR administrators can whitelist the banned IP addresses as well.
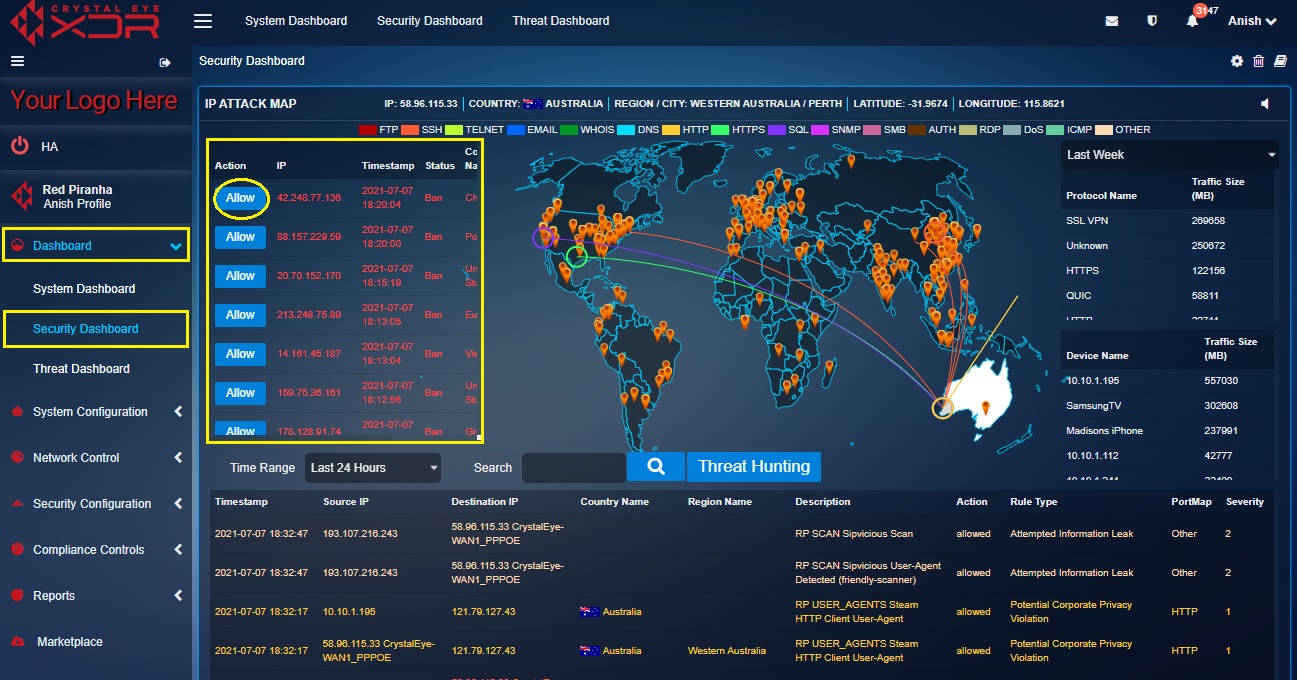
The following screenshot shows the Banned IPs Table:
Note
The Banned IPs Table can also be viewed in the IP Attack Map application. The banned IPs can also be allowed (whitelisted) from this application. A PDF report showing pie charts of the number of IP addresses banned and unbanned can also be obtained under the Banned IPs Logs Report section of the Forcefield application. The pie chart also shows the top 10 countries from where the IP addresses were banned.
How to Allow/Whitelist an IP Address Banned by Crystal Eye XDR’s Forcefield?
Step 1: In the Security Dashboard, click the Allow button next to the IP address that needs to be whitelisted in the Banned IPs Table.
Note
You will also notice that the banned IP address is erased from the Banned IP Logs Reports in the Forcefield application.
Real Time Attack Tracker¶
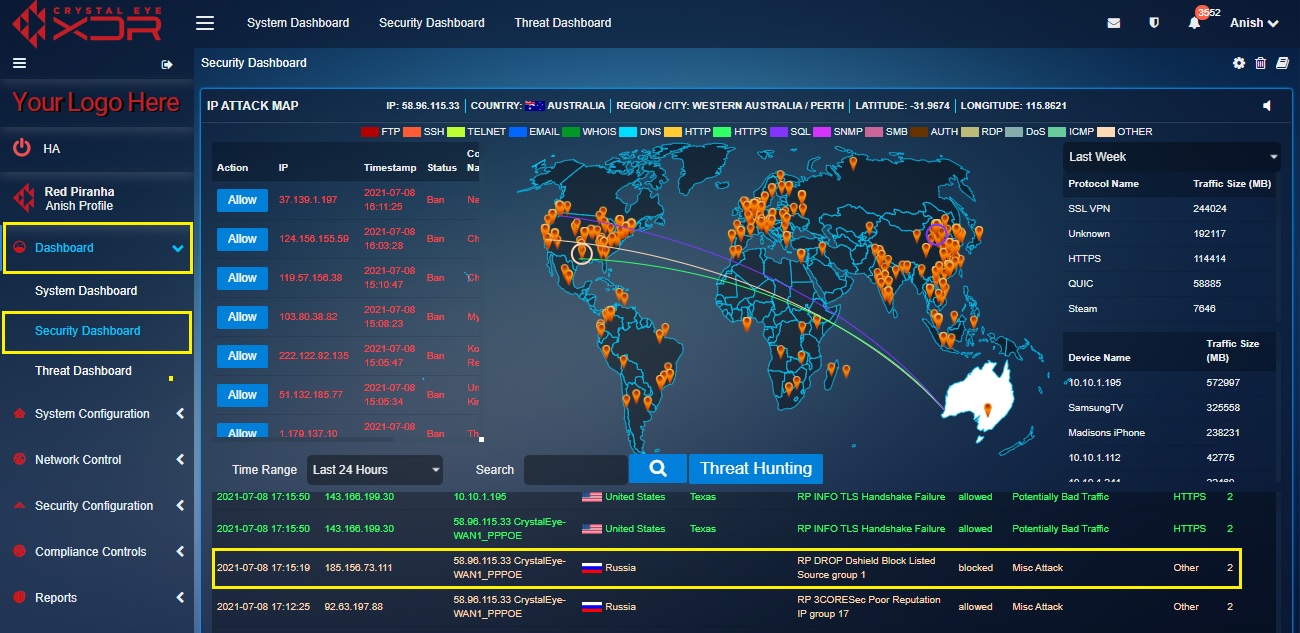
This part of the IP attack map provides specific inputs on the different types of attacks targeted towards Crystal Eye XDR networks. These attacks are derived Intrusion Detection and Prevention System (IDPS) Alerts. The strings of attacks as shown in the screenshot below are colour coded to specify different protocols used to execute the attacks.
Note
The Real Time Attack Tracker can also be viewed in the IP Attack Map application. The banned IPs can also be allowed (whitelisted) from the IP Attack Map application of the Crystal Eye XDR.
Some of the attack protocols that are detected and displayed here are FTP, SSH, TELNET, EMAIL, WHOIS, DNS, HTTP, HTTPS, SQL, SNMP, SMB, AUTH, RDP, DoS, and ICMP. If the attack protocols are different from the ones mentioned above then it would be recorded under ‘others’.
Each IDPS alert denoted in the world map has a corresponding effect on the Alert table. This table shows the date/time the attack was initiated, the source IP, destination IP, country (from where the attack originated), region name, description of the attack, severity etc.
Protocol Traffic Size Indicator¶
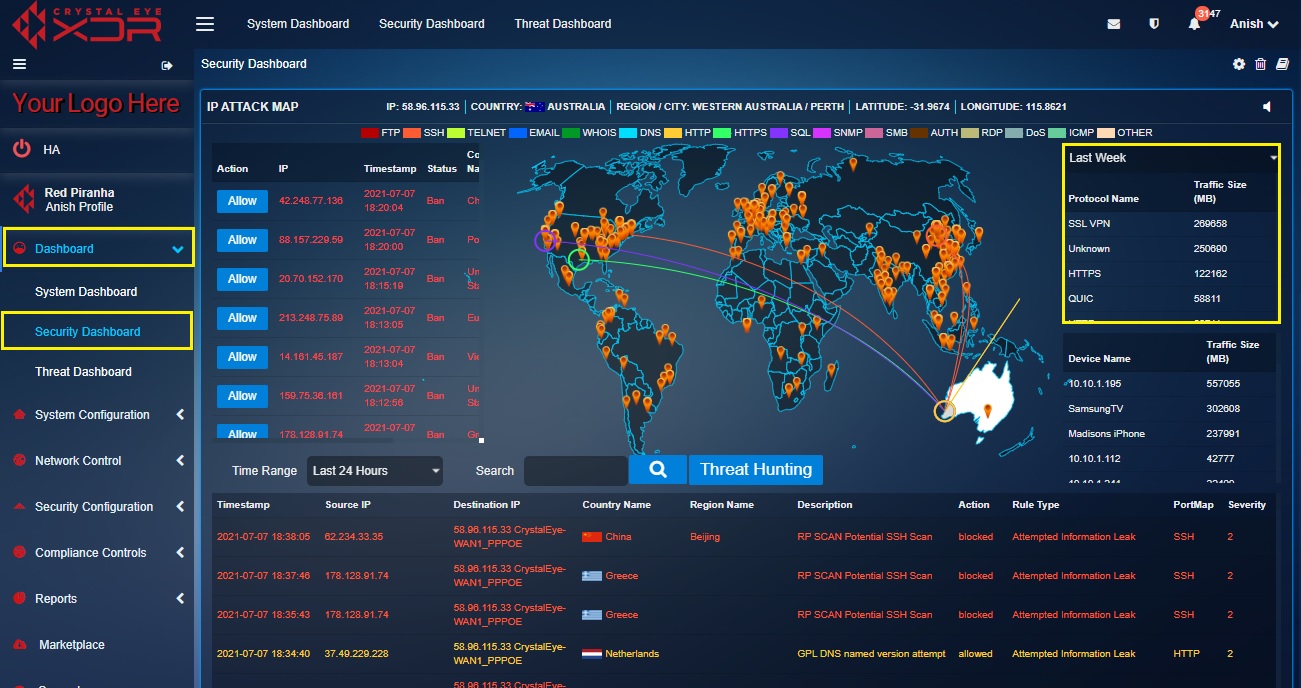
The traffic size or the size of the data transferred using a particular protocol is detected by the Crystal Eye XDR and is measured in megabytes and is displayed here in the Protocol Traffic Size Indicator table. The standard unit of measurement used to measure the Protocol Traffic Size is Megabytes (MB)
Note
The Protocol Traffic Size Indicator table can also be viewed in the IP Attack Map application.
Device Traffic Size Indicator¶
This table shows the device name (as mapped with the CE XDR) and the amount of data that it had received and sent over a period. The Device Traffic Size is measured in Megabytes (MB).
Note
The Device Traffic Size table can also be viewed in the IP Attack Map application.
Real Time IDPS Alerts¶
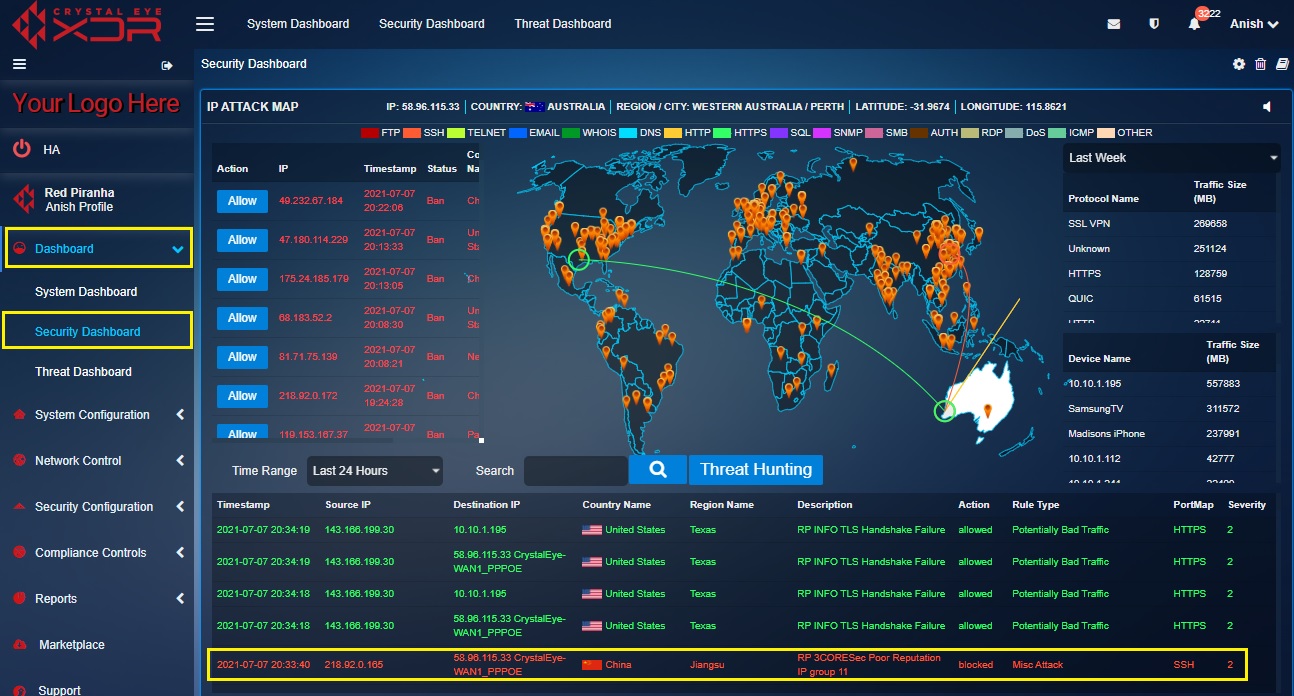
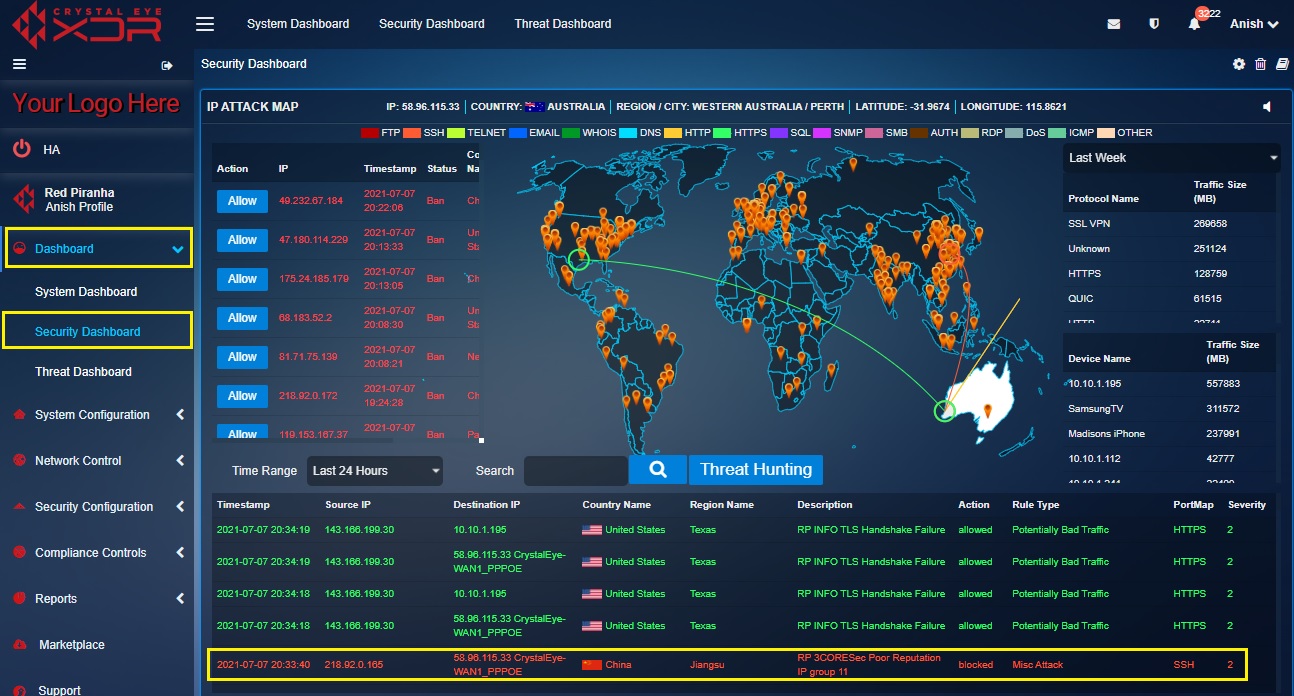
The Real Time IDPS Alerts section displays attack specific data also known as IDPS alerts generated on a real-time basis. These attacks and the protocols involved are visually depicted in the Real Time Attack Tracker mentioned above. When an attack is initiated, the origin of the attack and the target CE XDR network is visually depicted in the Real Time Attack Tracker. The Crystal Eye XDR administrator can also view elaborated details of the attack such as the source IP, destination IP, country (from where the attack originated), region name, description of the attack, severity etc in the Alert Report.
The above screenshot depicts that there was an attack that originated from United States and was targeted towards a network secured with Crystal Eye in Western Australia. The attack is denoted in the map and its corresponding details are also mentioned in the Alert Report.
Upon clicking a particular IDPS alert the Crystal Eye XDR administrator can view alert details, escalate an attack alert to Red Piranha’s SOC team, and view the IDPS rules that triggered the alert.
Note
The IDPS Alerts Report can also be viewed in the IP Attack Map application and the Threat Dashboard.
What is Alert Analysis? What are the various ways IDPS alerts can be analysed?
The Crystal Eye XDR displays various real-time alerts that can be viewed and analysed. The analysis process includes viewing the IDPS Alerts and the rules that are triggering these alerts. The real-time alert pops-up in the alerts report and is triggered by rules which can be converted to pass, drop, or reject. If a rule is triggering too many false positives then the Crystal Eye XDR administrator can also disable those rules. As a part of an elaborated alert analysis mechanism the CE XDR administrator also has the leverage to escalate an alert attack to Red Piranha’s security operations centre (SOC) team.
We have discussed the various ways to analyse IDPS alerts below (refer to the ‘how tos’ below):
- How to view IDPS alert details and the rules that triggers the IDPS alerts?
- How to convert the IDPS rules to Drop, Pass or Alert after it triggers an attack alert?
- How to disable a particular IDPS rule that triggers an IDPS alert?
- How to escalate an attack alert to Red Piranha’s security operations centre team for analysis?
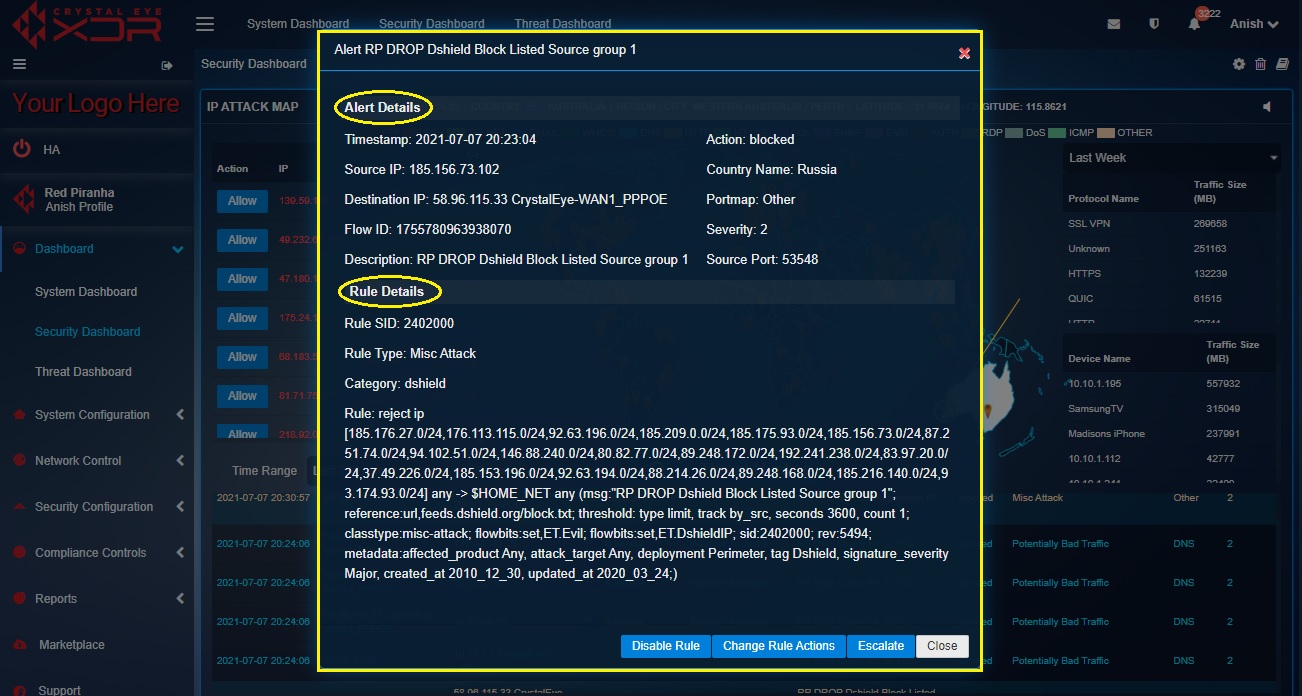
How to view IDPS alert details and the rules that triggers the IDPS alerts?
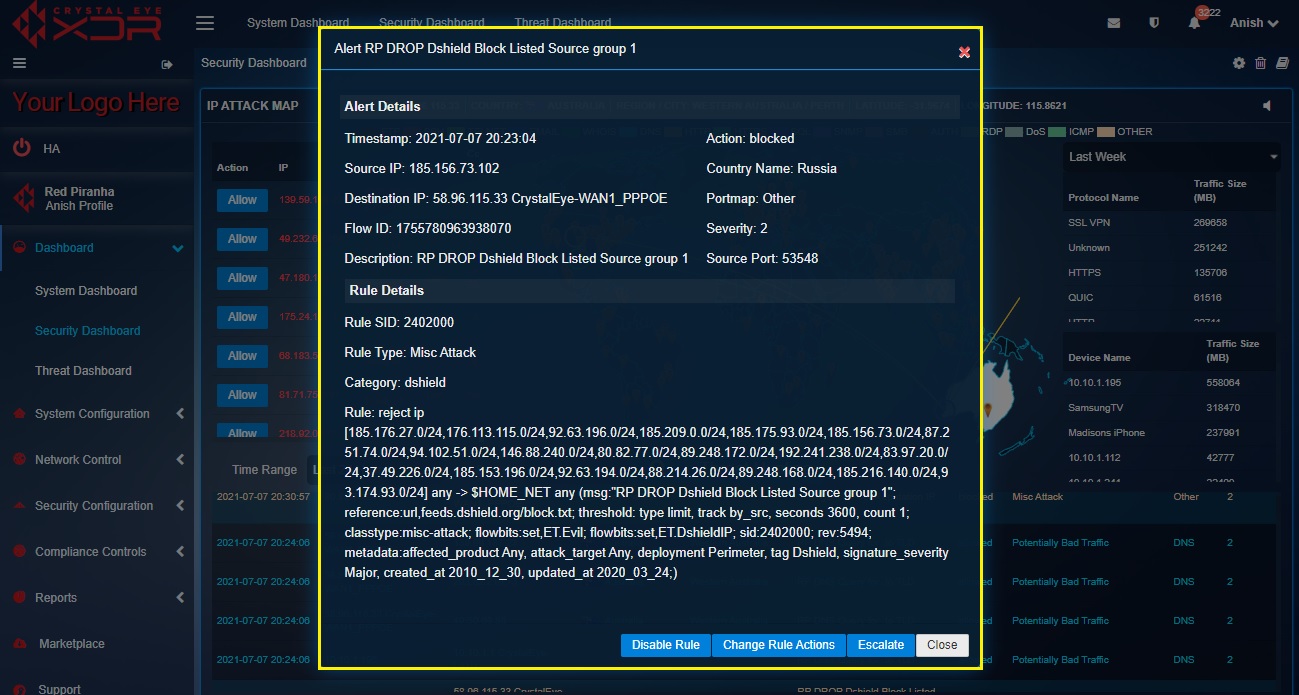
Step 1: In the Security Dashboard, click any of the IDPS alerts in the Alert Report section.
Step 2: You will now see a detailed report of the IDPS alert details and the IDPS rule details that triggered the alert.
How to select an appropriate action for the selected ruleset?
The IDPS rule plays a vital role in alerting and blocking detected anomalies in the Crystal Eye XDR network. The characteristics of these specially crafted rules can be changed as per required.
These rules can be converted to Alert, Pass, and Reject further defining the nature of the rules as discussed below.
Alert: After the action for the selected ruleset is set as ‘Alert’, the data packet will be detected, and an alert will be generated for the same.
Pass: After conversion of the rule action to Pass, if a signature matches, the packets are allowed by this rule and continue to be processed by subsequent rules in order.
Reject: Post conversion of the rule to Reject, if a signature matches then the packet will not go through, and both the sender and receiver will receive a reject packet.
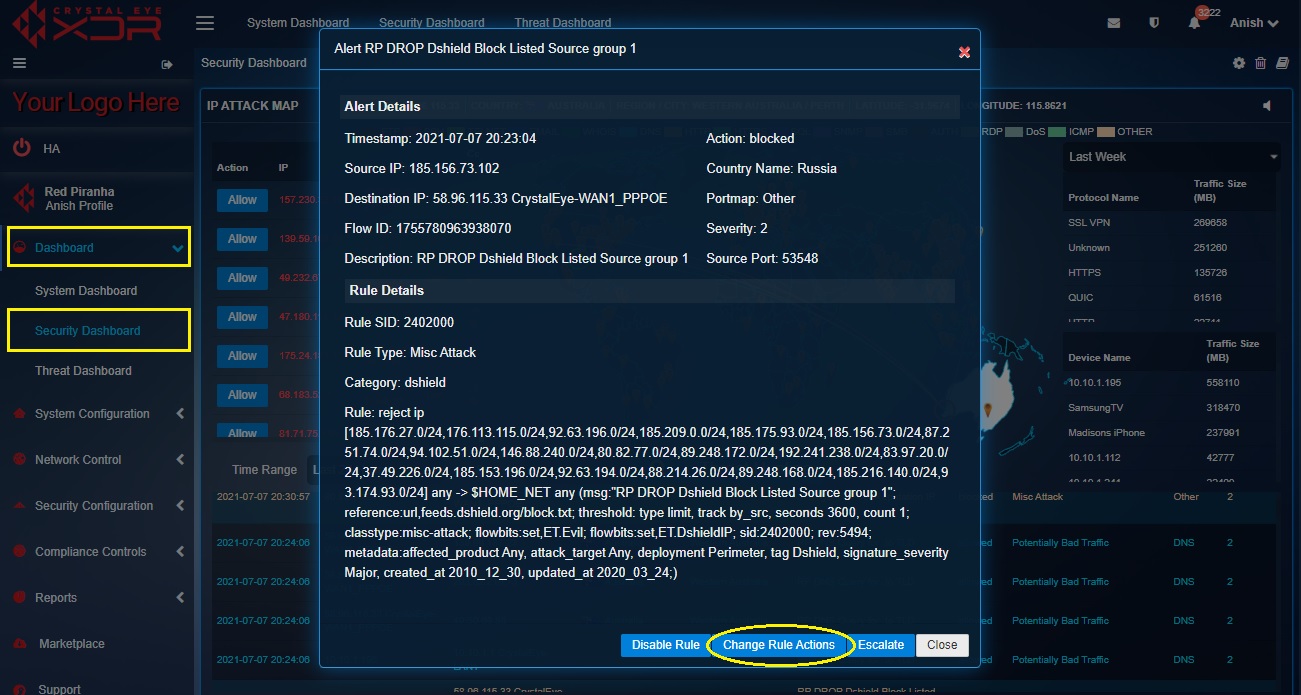
Step 1: In the Security Dashboard, click an IDPS alert in the Alert Report.
Step 2: You will now see a detailed report of the IDPS alert details and the IDPS rule details that triggered the alert.
Step 3: Click the Change Rules Actions button in the IDPS alert details pop-up.
Step 4: You will now see the Change Rule Actions pop-up. Select Alert, Pass or Reject from the default_ruleset dropdown and click the Update button. 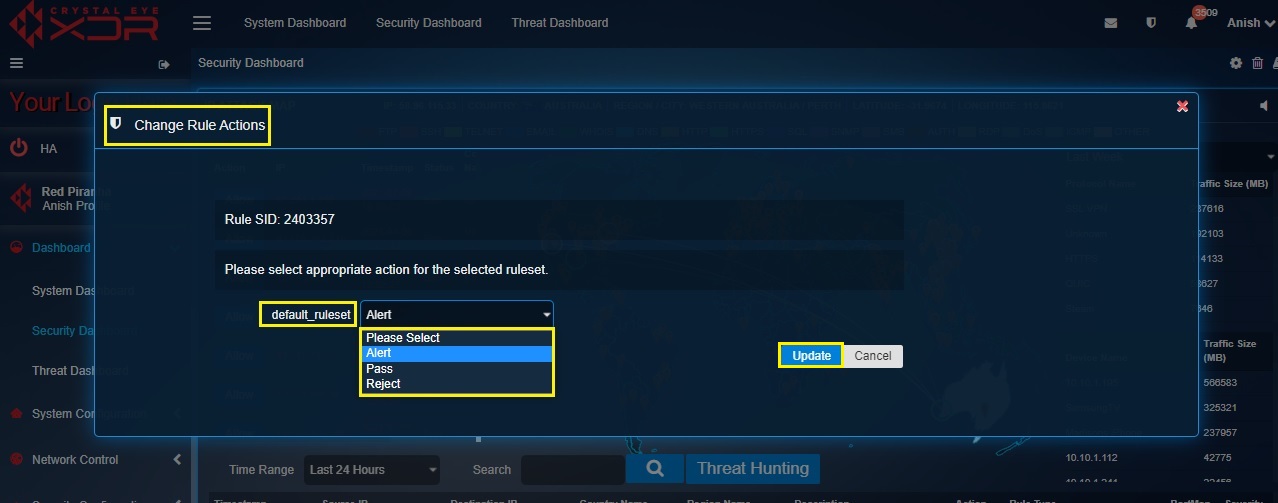
Note
If there is a requirement to dig in deeper to further analyse the IDPS Alerts in detail then this can be done by hitting the Threat Hunting button. You will then be directed to the IDPS Threat Hunting section of the Threat Dashboard. 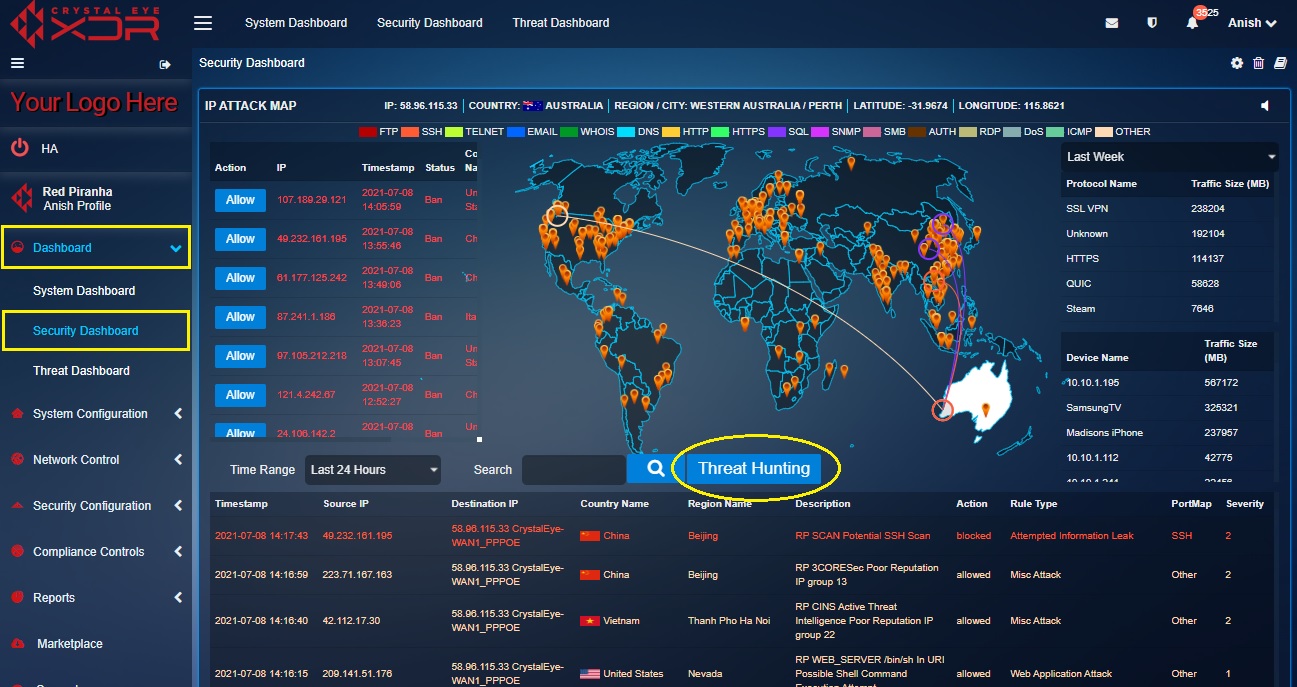
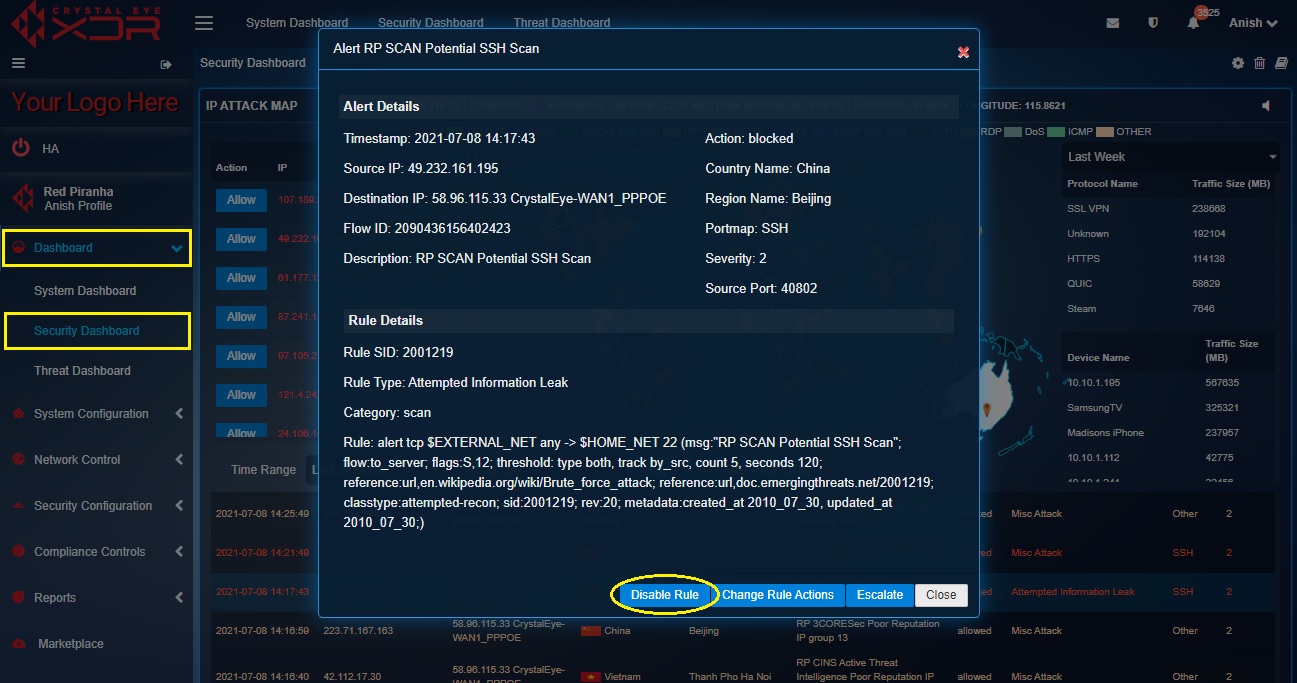
How to disable a particular IDPS rule that triggered an alert?
The Crystal Eye XDR administrator might come across situations when the IDPS rule that triggered the alert must be disabled. In this case, the IDPS alert must be clicked and then the Disable Rule button must be clicked.
Step 1: In the Security Dashboard page, click the IDPS alert for which the IDPS rule needs to be disabled.
Step 2: You will now see the Alert Details and the Rule Details. Read the details and then click the Disable button.
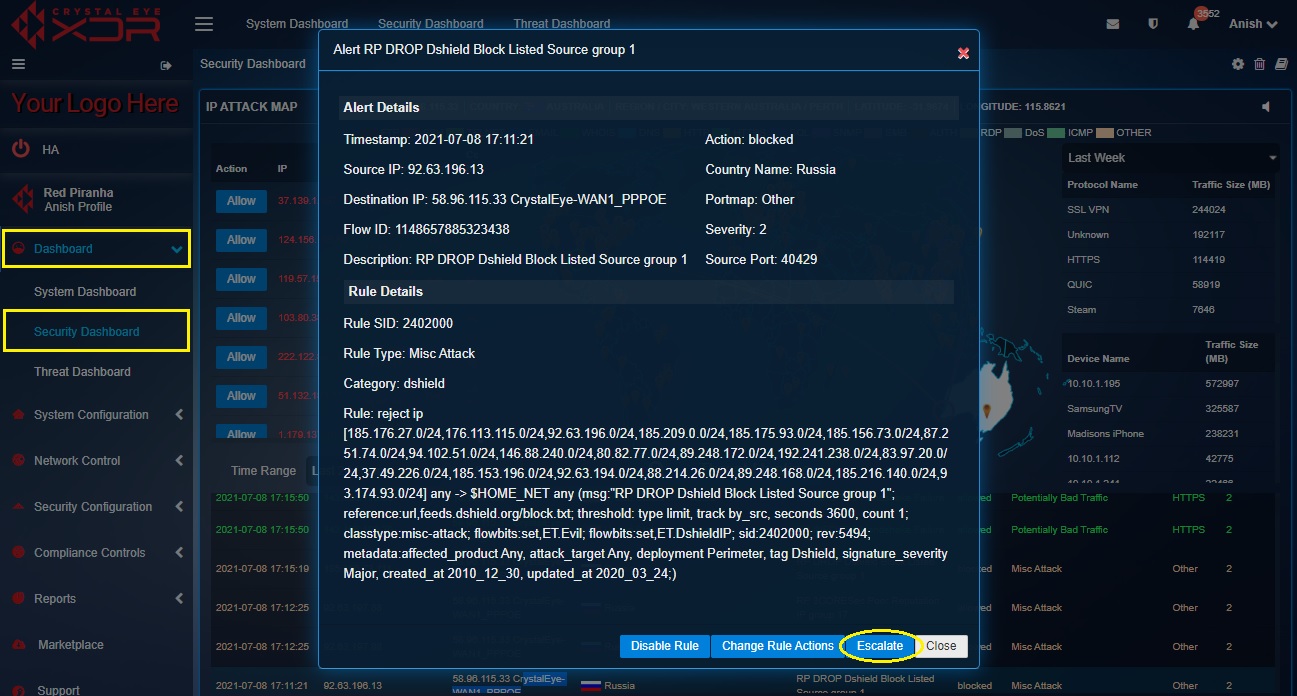
How to escalate an attack alert from the Security Dashboard to Red Piranha’s security operations centre (SOC) team for analysis?
All attack alerts can be escalated to Red Piranha’s Security Operations Centre (SOC) Team after the Incident Response Services application is installed.
Note
Escalations will not be processed until the Incident Response Services application is installed and configured.
The details of the alerts that are escalated are also displayed in the Escalated Alerts section under the AI and Escalation Reports tab of the Threat Hunt Dashboard. A PDF report of the Escalated Alerts can also be generated from the escalated alerts section.
Click here to know how to configure Incident Response Services application.
Note
If the Incident Response Services application is not installed and configured then the following error message will be displayed.
Step 1: In the Security Dashboard page, click the IDPS alert that needs to be escalated.
Note
Before you initiate the process of alert escalation to Red Piranha’s SOC team make sure that the Incident Response Services application is installed and configured. Click here to know how to configure the Incident Response Services application.
Step 2: You will now see the Alert Details and the Rule Details. Read the details and then click the Escalate button.
Step 3: You will now see a Comment Box. Add the comment and click the Submit button.