Threat Summary
Overview¶
The overview dashboard is an excellent setup to monitor a variety of variables that influence organizational threat hunt tasks. The data collected in the overview dashboard helps in continuous monitoring of indicators that determines whether there is an eminent cyber threat existing in the network.
Navigation to the Threat Summary¶
Go to Dashboard > Threat Hunt Dashboard > Summary
Alerts Over Time¶
The "Alert Over Time" graph shows the number of alerts against the selected interval of time.
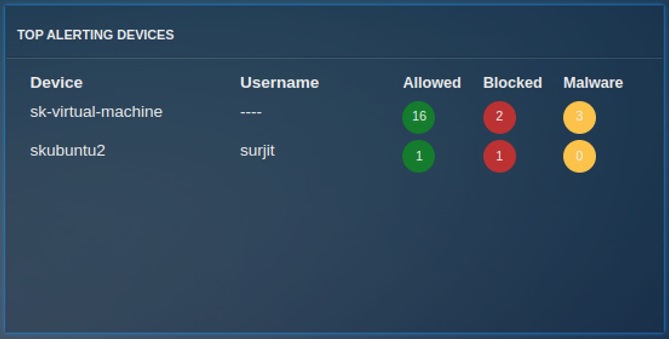
Top Alerting Devices¶
The "Top Alerting Devices" table shows the data of Top alerting devices in the selected interval of time. This table contains Device Name/Host Name for Mapped/Unmapped devices respectively, the Username, and Allowed/Blocked/Malware count.
Top Alerting Countries¶
The "Top Alerting Country" graph shows the top 10 list of countries and their respective alert count in the selected interval of time. Whereas, the table shows the top 10 list of IPs, their respective country and alert count.
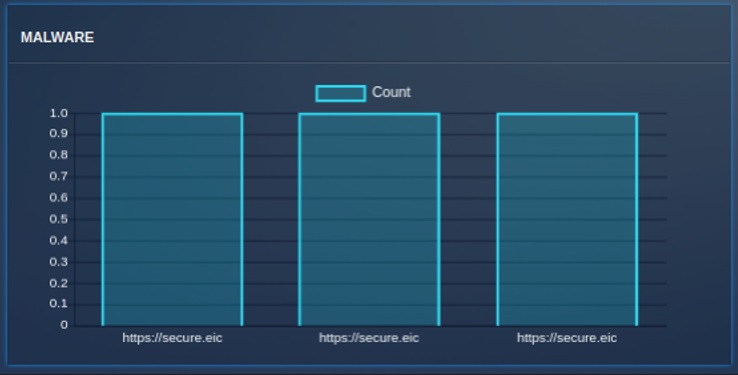
Malware¶
The "Malware" graph shows the top 10 Malware and their respective count in the selected interval of time.
Top SIDs¶
This pie chart shows the top SIDs triggered in the Crystal Eye XDR network. Signature Identity (SID) is a unique identification number auto assigned to an IDPS Policy rule. These rules are conceptualised and created by the security operations team of Red Piranha to provide context to the Intrusion Detection & Protection (IDPS) mechanism of the Crystal Eye XDR.
One of the most important functions of the IDPS signature rules is to specify the component of the network traffic that the system must inspect to detect attacks. An IDPS action is triggered if a rule is matched with specific pre-defined attack patterns. The IDPS system performs the assigned action which helps in protecting the Crystal Eye network.