Azure Threat Hunting
Overview¶
Monitoring Azure Active Directory (Azure AD) events can help you track changes and activities in your Azure AD environment.
This can be useful for a variety of reasons, such as:
Ensuring the security of your Azure AD environment: By monitoring Azure AD events, you can identify potential security threats, such as unusual login activity or unauthorized changes to user accounts.
Troubleshooting issues: Monitoring Azure AD events can help you diagnose and resolve problems in your Azure AD environment. For example, if you notice a spike in failed login attempts, you can use this information to investigate the cause and take appropriate action.
Auditing and compliance: Many compliance regulations require organisations to track and audit certain activities in their IT systems. Monitoring Azure AD events can help you meet these requirements by providing a record of changes and activities in your Azure AD environment.
Overall, monitoring Azure AD events can provide valuable insights and help you maintain a secure and efficient Azure AD environment.
Active Directory Audit Report¶
The Active Directory Audit Report provides a glimpse of the Logged in Users details, various user based operations, logon errors, result status and the location of the users.
Logged in Users¶
This monitoring parameter reflects the number of time user’s login to their accounts over a period. It also specifies the total login’s done using each email ID.
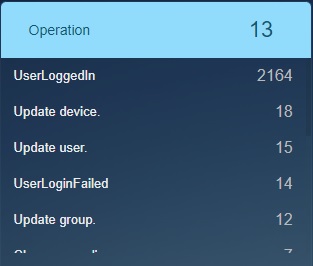
Operation¶
The following operations are recorded by the Crystal Eye XDR:
UserLoggedIn: This is the total number of times all users have logged in.
Update device: This specifies the total number of times a device was updated.
Update user: This parameter helps in knowing the total number of times a user was updated.
UserLoginFailed: For failed logins (where the value for the operation property is UserLoginFailed), this property contains the Azure Active Directory STS (AADSTS) error code.
Update group: This is the total number of times a group was updated over a period.
Change user license: The total times a user license was changed.
Change user password: The number of times a user password was changed over time.
Add member to group: The total number of times a member to a group was added.
Add user: Total number of times a new user was added.
Delete device: Total number of times a device was deleted.
Device no longer managed: Total number of times a device management is haulted.
Restore user: Total number of times users were restored.
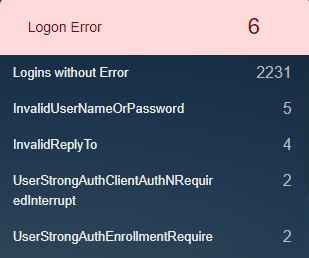
Logon Error¶
This monitoring parameter provides insights of the different Logon Errors that might have popped up while users logged in. One of the most important stats results is the total number of error-free logins that took place over a period recorded under ‘Logins without Errors’.
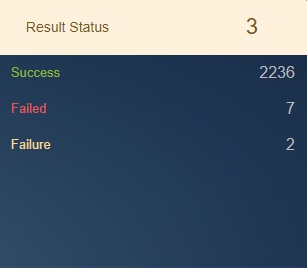
Result Status¶
The result status indicates whether the action (specified in the operation property) was successful or not. Possible values are Succeeded, Partially Succeeded, or Failed. For Exchange admin activity, the value is either True or False.
Usage Location¶
This monitoring parameter shows the location from where user activities were recorded.
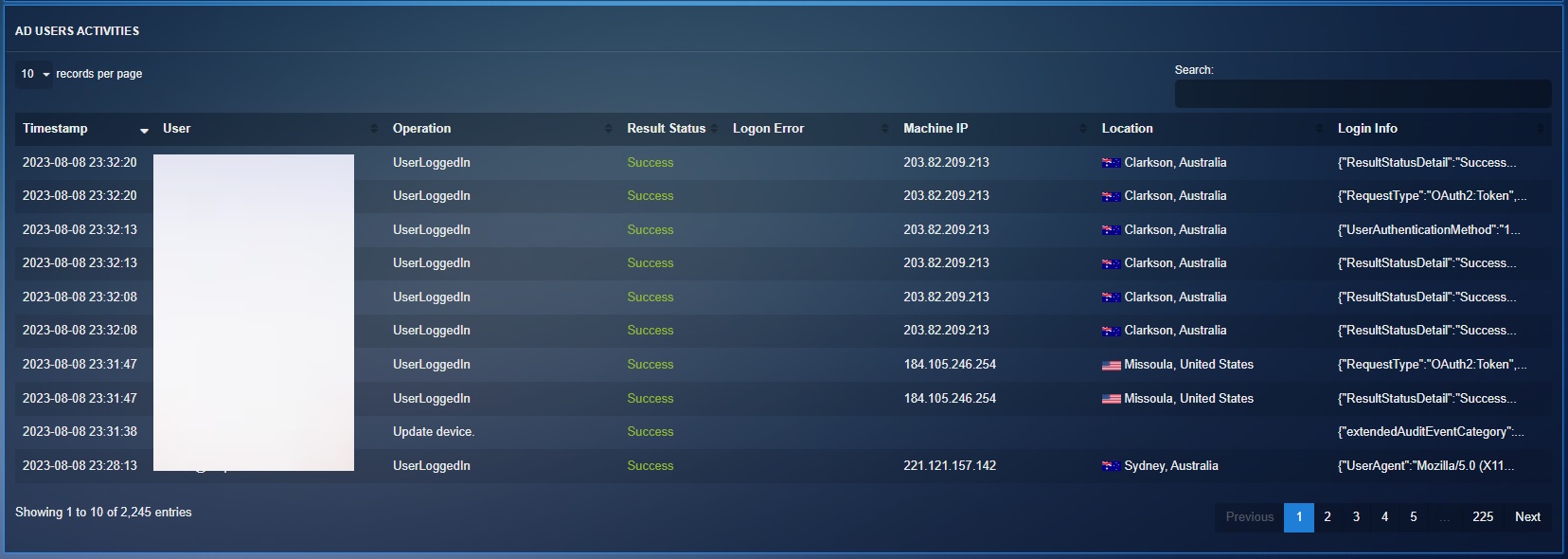
Aggregated Active Directory Users Activities¶
This section helps in corelating the result status with the users, their machine IP, geographical location, and the provides an in-depth view of the Logon Error types.
Important
The Result Status Indicates whether the action (specified in the operation property) was successful or not. Possible values are Succeeded, Partially Succeeded, or Failed. For Exchange admin activity, the value is either True or False.