Defender for Endpoint
Overview¶
Defender for Endpoint stands as a comprehensive and sophisticated endpoint security solution deeply embedded in the Crystal Eye XDR network. This advanced platform goes beyond traditional antivirus measures, offering real-time protection against an array of threats, including viruses and ransomware. Leveraging continuous updates and state-of-the-art threat intelligence, Defender for Endpoint remains vigilant, actively scanning, and promptly neutralizing potential risks to ensure a secure computing environment.
Tailored for corporate networks, this solution becomes a linchpin in cybersecurity strategies, providing robust protection for endpoints. Its user-friendly interface and seamless integration with Microsoft 365 systems facilitate ease of use, making it an indispensable tool for organizations seeking to fortify their digital defences against the ever-evolving landscape of cyber threats. Defender for Endpoint stands as a stalwart guardian, embodying Red Piranhas commitment to ensuring the security and integrity of endpoint devices.
Installation¶
The Defender for Endpoint application is not available by default. It can be installed from Marketplace in the left-hand navigation panel.
Navigation to the Defender for Endpoint Application¶
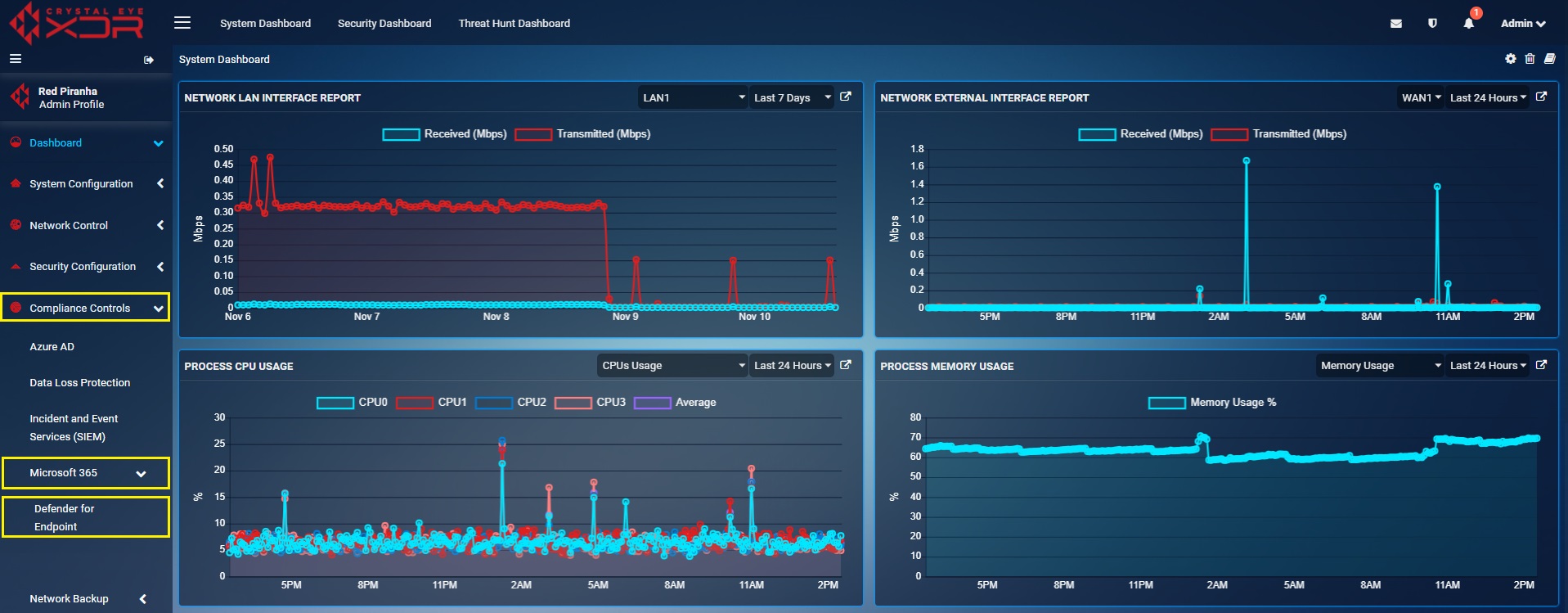
Go to Compliance Controls > Microsoft 365 > Defender for Endpoint
Configuring Crystal Eye XDRs Defender for Endpoint App¶
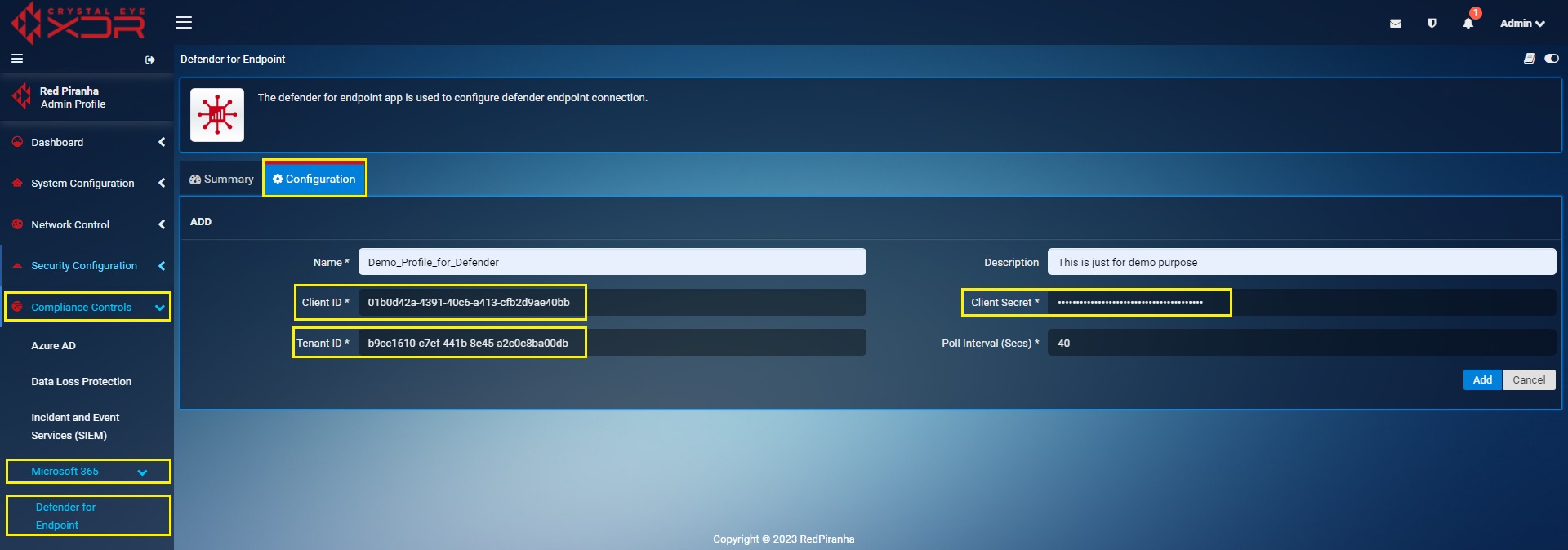
The configuration parameters in the Crystal Eye XDR Defender for Endpoint app constitutes of 4 components that can be copied/extracted from the Microsoft 365 Portal. To do so, the first requirement involves creating an application in the Microsoft 365 portal.
Note
After registering an application in the Microsoft 365 portal, we will extract the Client ID, Tenant ID, Client Secret and enter it in the field highlighted in the screenshot below.
Perform the following steps to integrate the Microsoft 365 platform with the Crystal Eye XDR to view the various threats detected.
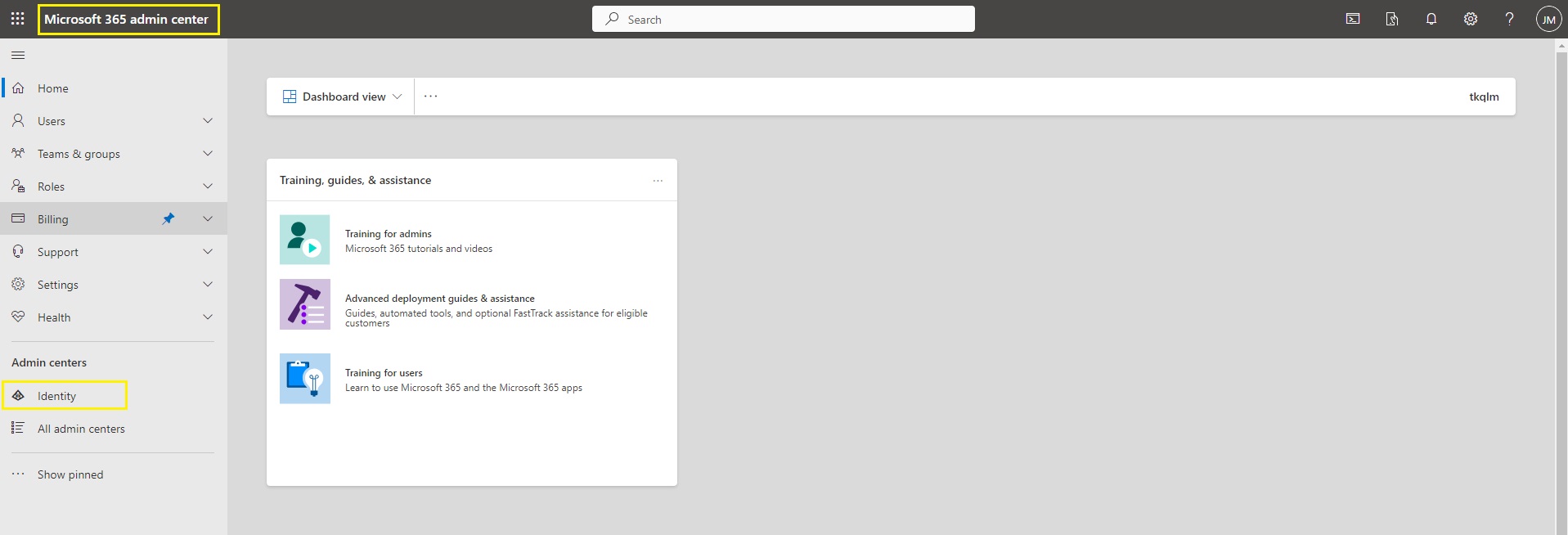
Step 1: Login to your Microsoft 365 admin center and select Identity in the navigation menu.
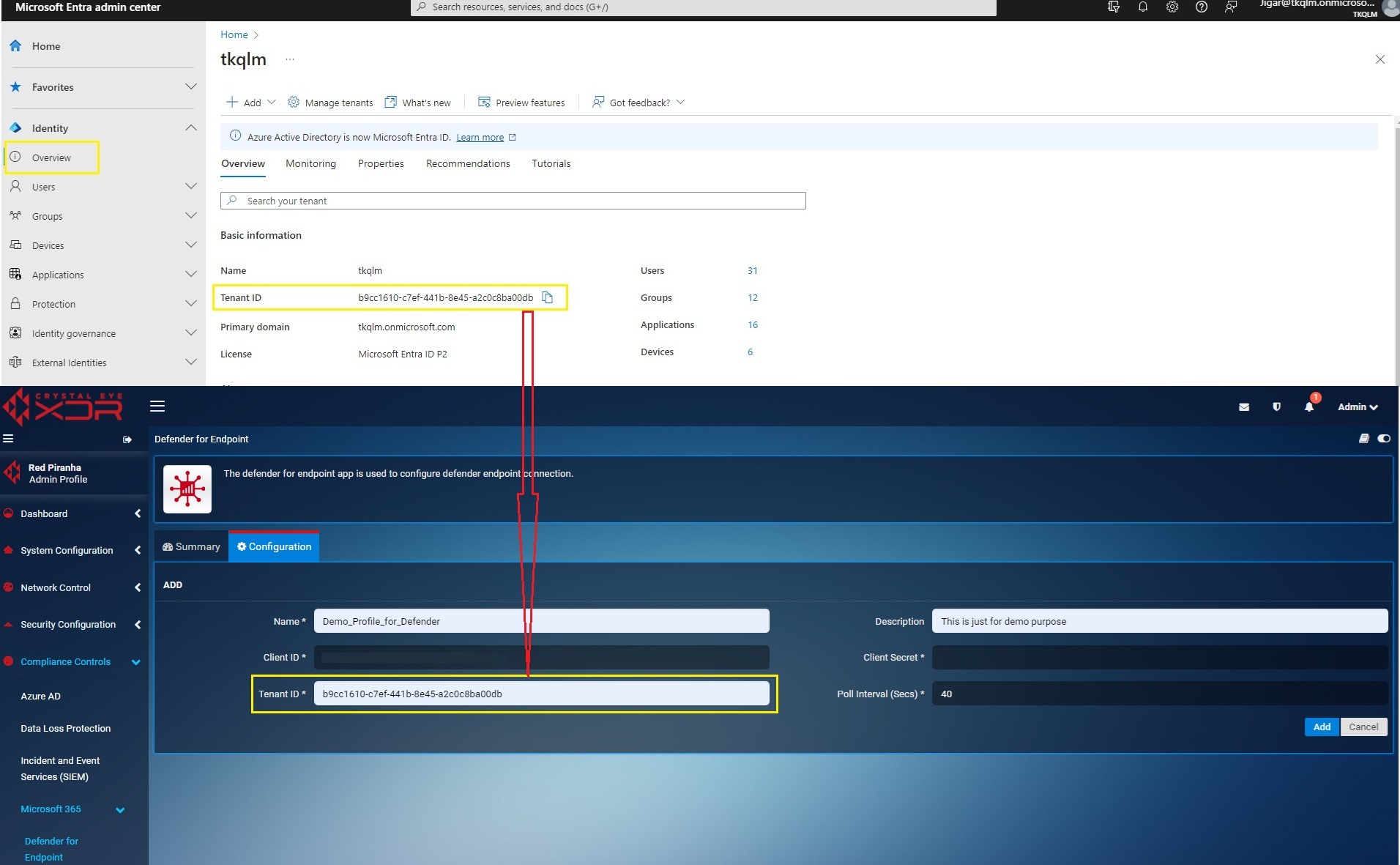
Step 2: You will be directed to the Microsoft Entra admin center. Click Overview in the navigation menu. You can find the Tenant ID here. Copy the Tenant ID. Now login to your Crystal Eye XDR and go to Compliance Controls > Microsoft 365 > Defender for Endpoint > Configuration Tab. Paste the Tenant ID (copied from the Microsoft 365 portal) to the Tenant ID textbox in the CE XDR user Interface as shown in the screenshot below.
Step 3: Click the New registration button in the top-panel by navigating to App registrations under Applications tab.

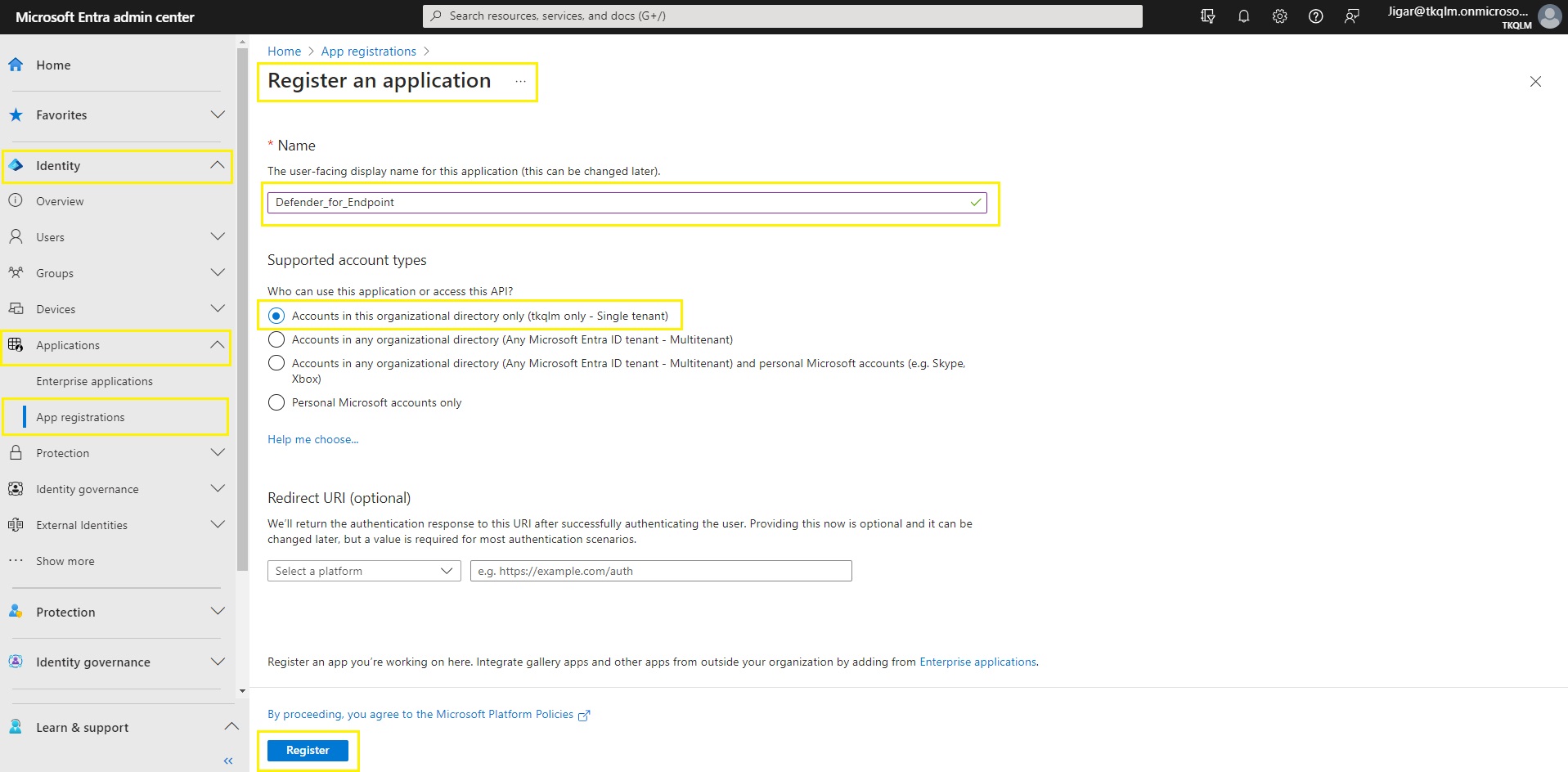
Step 4: You will be directed to the Register an application. Enter an application name in the Name textbox. Select the radio button, “Accounts in this organizational directory only (single tenant)” and click the Register button.
Step 5: You will see the message, “Successfully created application”. Click Enterprise applications in the navigation menu and the created application will now be visible in the applications list. Click on the application you have created.

Step 6: You will now be directed to the Application Overview page. Copy the Application ID. Now login to your Crystal Eye XDR and go to Compliance Controls > Microsoft 365 > Defender for Endpoint > Configuration Tab. Paste the Application ID (copied from the Microsoft 365 portal) to the Client ID textbox in the CE XDR user Interface as shown in the screenshot below.

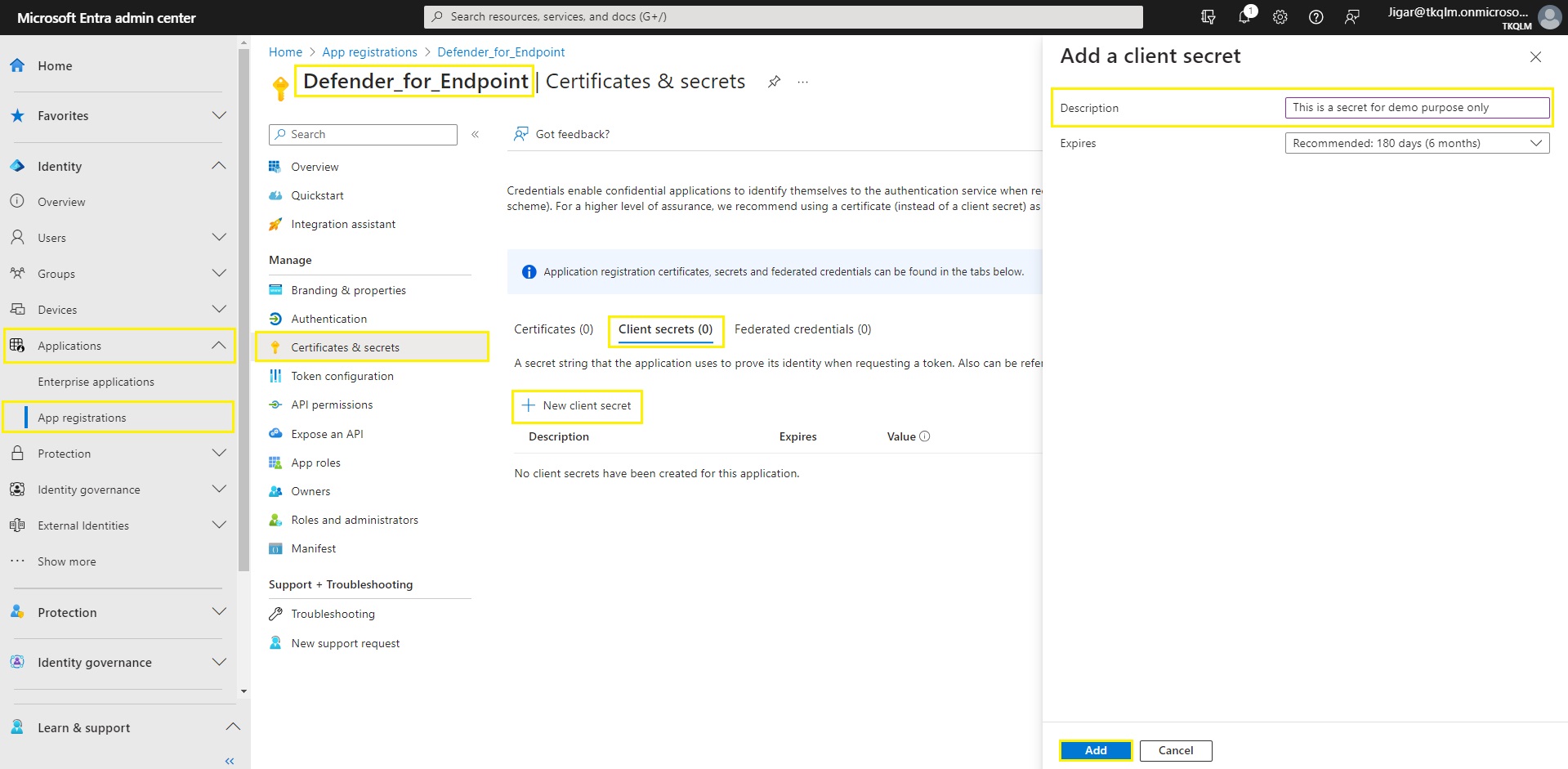
Step 7: Go to App registrations > Defender_for_Endpoint > Certificates & secrets > Client secrets tab in the navigation menu. Click on New client secret button.

Step 8: Enter the description in the text box for creating the secret and click the Add button.
Step 9: The newly created secret will now be visible under Client Secrets tab.
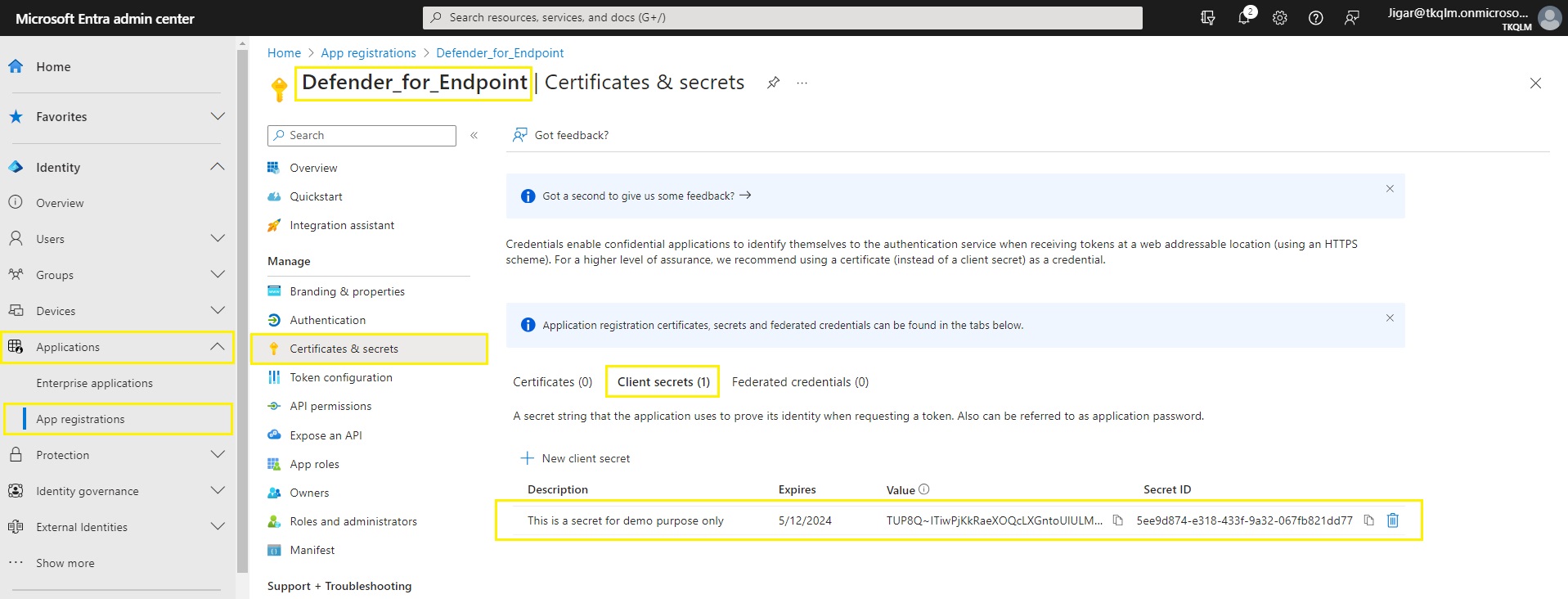
Step 10: Copy the secret value and paste it in the Client Secret textbox in the CE XDR user interface.

Note
This Client secret value is visible only once. Make sure to save its value wherever possible.
Step 11: Copy the secret value. Now login to your Crystal Eye XDR and go to Compliance Controls > Microsoft 365 > Defender for Endpoint > Configuration Tab. Paste the secret value (copied from the Microsoft 365 portal) to the Client Secret textbox in the CE XDR user Interface and click the Add button.

Step 12: The created configuration will now be visible under Configuration tab.

Summary report of Crystal Eye XDRs Defender for Endpoint App¶
The Summary report displays the Timestamp, Title, Investigation State, Threat Name, Detection Source, Category, Severity and Status of the Events captured by defender application as shown in the screenshot below.
Timestamp: It shows the timestamp of the event logs in YYYY-MM-DD HH:MM:SS* format.
Title: It shows the title of the event logs captured such as Information stealing malware activity, Suspicious activity linked to an emerging threat actor has been detected, Malicious document detected, 'CVE' ransomware was prevented and many more.
Investigation State: It shows the current state of the Investigation such as Terminated by System, Unsupported Alert Type, Successfully Remediated, Partially Remediated.
Threat Name: It shows the Names of the threat which are detected by the Defender App.
Detection Source: It shows the Source of the detection from the event logs are detected.
Category: It shows the various categories of the Event logs such as Credential Access, Defense Evasion, Exploit, Initial Access, Lateral Movement, Malware, Ransomware and Suspicious Activity.
Severity: It shows the Severity of the event logs whether it’s High, Medium, or Low.
Status: It displays the status of the event logs whether it’s a New log or the log has already been Resolved.